Control your business data on any device with Zero Trust as the cornerstone of your security
If there’s one struggle IT faces it's the rise in the use of BYO and unmanaged devices. On the one hand, letting employees and contractors bring their own device for work can go a long way in reducing costs and simplifying IT. But at the same time, IT has to ensure company data isn’t compromised. And while corporate-owned devices can be closely monitored, a lack of insight into the health of unmanaged devices creates a significant risk.

There are a variety of pros and cons to a BYOD model for both employers and employees. Some of the benefits include:
However, there are some significant liabilities presented by a BYOD model, particular in terms of network security and safeguarding sensitive company information. Additional challenges to incorporating a BYOD framework include:
While increased support for remote work and BYOD has significant benefits for an organization, one cannot ignore the security implications. Mobile workers simply operate in different ways than traditional, on-site employees, introducing unique security risks and challenges to the organization.
There are many situations where a worker might need to access a company network on a device that is not owned and managed by the company. Freelancers and consultants may use their own PC’s and need remote access to a company’s IT resource. Other cases include:
-1.jpg?width=270&name=joseph-frank-XGC_1eH_ZGI-unsplash%20(1)-1.jpg)
Most enterprises support employees on the corporate network. However, it's inevitable that other users, such as 3rd-party business partners, will also work from within your corporate network. These situations spotlight the true reason why location-based security tools are woefully overrated and why security should be uniform across the board.
When bringing non-employees or 3rd parties into a corporate network, you should utilize the Zero Trust philosophy of “trust no-one outside or inside the network.” If the only security you have is at the network layer, granting 3rd-party access creates a giant security risk. However, if “identity is the new firewall,” it's important to make sure each identity (user) inside or outside the network only has the access they need, this to ensure the access to company resources remains secure. Read more

Managing the security of remote employees has been a major concern in the wake of the COVID-19 pandemic.
Security administrators are finding their edge security products provide no benefit to remote workers who use the internet to connect directly to private cloud resources. While it is possible to force remote workers through the corporate network to use VPN or virtual desktop infrastructure technologies, these options often prove inefficient and burdensome. Zero Trust becomes a great alternative because it does not require users to connect to the corporate network before accessing services. Read more

OT (Operational Technology) environments are mostly operated by management stations controlling multiple industrial devices, Programmable Logic Controllers (PLC’s) etc. These OT environments have a high demand for real-time operation. This requirement will mostly stand in the way of a decent security design. The resulting design is mostly a strict separation between OT and the IT environment. Port based bridges (firewalls) are created to enable access to this environment, with all the additional needed monitoring as a requirement to this approach.
Soliton's G/On will enable you to only allow the securely verified user to setup a connection to these OT management stations. All other connections are no longer needed or allowed. Resulting in a far lower amount of time spend on monitoring these sessions. Read more
Soliton's Enterprise Access solutions are about securely enabling applications on unmanaged remote devices to access company internal applications and services. Our security model is built on the assumption: "The enemy knows the system" and assumes that the enemy will use targeted attacks.
The central services are protected inside a security perimeter, and can only be accessed through a gateway. Whereas the gateway will only present the allowed applications to the verified user with a per user dynamically generated menu.
Learn more about Soliton's enterprise access solutions for unmanaged devices:

Following are the most severe risks affecting unmanaged and BYO devices.
When employees use personal devices at work, any access to the corporate network can pose a risk. Attackers can gain access to a lost or stolen device or compromise a device via phishing or malware. At that point, attackers have three main options to do damage:
It is inevitable that employees will perform both work and personal tasks on their personal device. Your organization won’t have control over websites visited by employees or that they use unsecured wireless networks to connect —the list of potential threats is endless.
Smartphones are commonly infected by malware, and in most cases, smartphone users are not aware their phone is infected. Another threat is that users often install questionable applications.
Privacy and data sovereignty laws introduced common frameworks to manage and monitor compliance for a range of IT regulations and standards.
An increasingly diverse workforce of employees, partners, contractors, and other third parties coupled with unmanaged and BYO devices creates an additional security gap. Personal devices are typically unmanaged because the employee doesn’t want their organization monitoring their private device. Only with visibility into the use of your data on unmanaged and BYO devices will you avoid exposing your organization to unknown risks and close the security gap.
From its early beginning, Soliton's enterprise access solutions are designed with Zero Trust in mind:
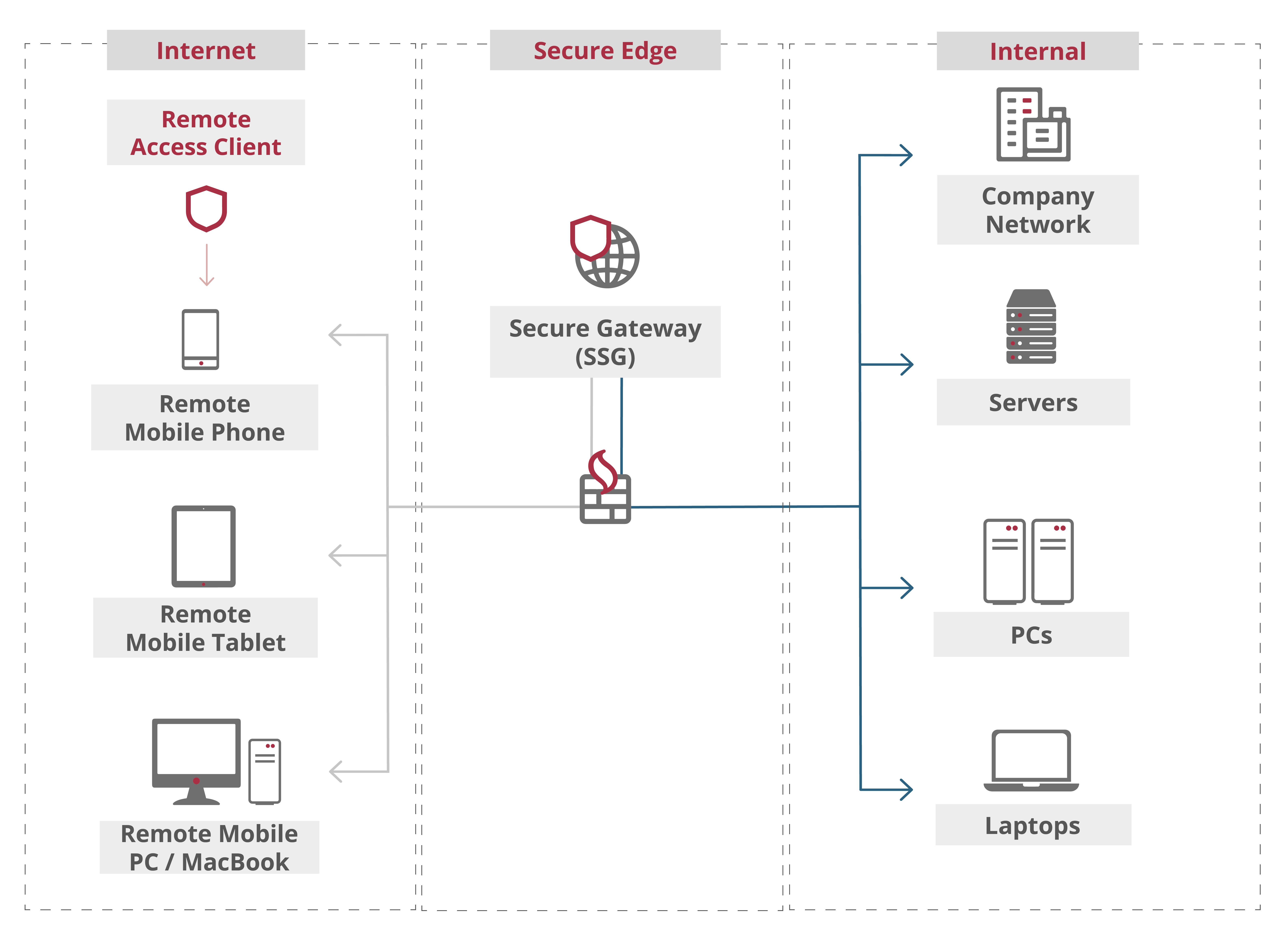
It seems that many businesses are confident in providing secure access for their remote workers, but are still relying on inherently insecure solutions such as Virtual Private Networks (VPNs).
VPNs are part of a security strategy based on the notion of a network perimeter; trusted employees are on the inside and untrusted employees are on the outside. VPN is good for internal employees who need to access the server from anywhere besides the office. However, there are a number of concerns and vulnerabilities when it comes to deploying VPN.
An alternative to VPN is “Zero Trust ” where nothing is trusted, unless it can prove explicit identification of who it is each time it connects. Explicit identification means a stringent 2-way authentication.
Remote workers take the freedom to process data in the way they like. They edit files, forward them to others and make screen-prints of sensitive information. Because you never know how safe the endpoint is, Soliton always implements a security layer around the work process of the end-user.
All company applications and data are segregated, users simply access the resources through the client app installed on their private device. The connection is always encrypted with strong mutual authentication, remote workers can connect to any Wi-Fi, only this time, risks are limited to a minimum. By applying the extra security layer the end-user and IT admin will have no fear of being at risk and allows employees to use any type of device and any type of internet connection.
A great benefit of this approach is that it eliminates Mobile Device Management (MDM). If you’re unsure about the best strategy to enable secure remote working, our white paper may be an interesting read.