In the consumer market, end-to-end encryption has become very popular in recent years. Messaging apps such as WhatsApp and Skype are household names with end-to-end encryption capabilities. However, the enterprise sector has been slower in adopting end-to-end encryption - though we do see some business communication platforms now, including end-to-end encryption to support customer security and compliance requirements.
Many companies rely on cloud providers to keep their data safe, while others set up their on-premise servers to ensure data remains within their physical boundaries. Those organisations that rely on the security measures offered by their cloud providers will find that this security provides data encryption at rest. Data becomes vulnerable if hackers access the providers' servers where encryption keys are stored because of E2EE stores encryption keys on user devices and not on servers. Access to encrypted data during such a breach would not be possible.
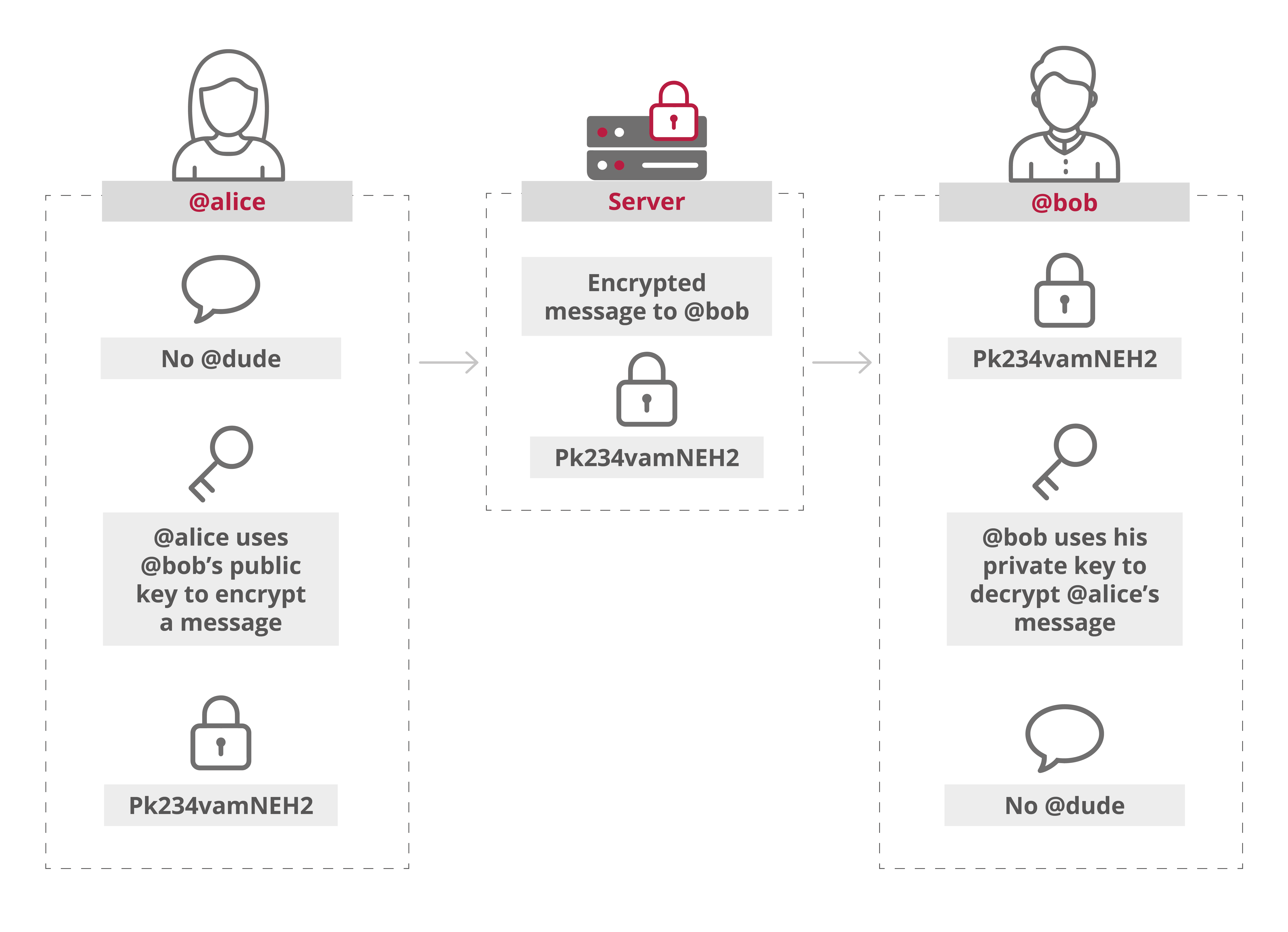
In theory, hackers can intercept the message in transit, and service providers can access the encrypted message to store it. But the message will appear unintelligible gibberish, as the original contents are only visible to the sending and receiving devices. No other interceptors (hackers, service providers, or anyone else) have the correct keys to decrypt the message.
This practice ensures data is only viewed in its true form on the sending and receiving devices and nowhere in between.
Some E2EE implementations enable the encrypted data to be decrypted and re-encrypted at certain points during transmission, which is why Soliton's solutions clearly define the endpoints of the communication circuit.
During transit, messages are encrypted and impossible to read. But information about the message (date sent and recipient, for instance) is still visible. This provides vital information for Data Protection Officers to ensure data stays within allowed endpoints.
If endpoints are compromised, there is a risk encrypted data may be revealed. This is why Soliton has the Zero Trust embedded in all its solutions, either preventing data from residing on endpoints or storing it in an encrypted container.